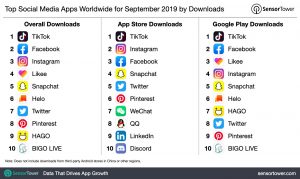
What are the tips and tricks to number hacking?
So would you like to realize how to hack a telephone without them knowing? This guide will take a gander at a few different ways to hack somebody’s phone in 2020. I’ll begin with the least difficult and afterward investigate some option hacking techniques that you may not think about. First we should clarify what telephone hacking truly implies. Most word reference definitions – hacking signifies “unapproved admittance to information on a framework or PC”. In the event of PDA hacking – telephone framework or PC.
Presently I’m not totally alright with the term hacking in light of the fact that it has some illicit meanings. In the event that you follow this site you will realize that I take a top to bottom gander at phone spy programming applications – exploring the most famous applications, disclosing how to utilize them; I am continually checking.
Legitimate methods to number hacker
This should be possible through legitimate methods. I don’t advance any unlawful utilization of spy applications. In the event that you can hack somebody’s telephone, you fundamentally approach everything in it – it’s a door to hacking web-based media accounts, passwords, courier applications and that’s just the beginning.
Call it hacking or spying or observing somebody’s PDA. They all have a similar outcome – admittance to information. So how would you do that?
Rundown box
As a rule the general purpose is to hack somebody’s telephone without them knowing and still approach however much information as could reasonably be expected – concurred? Phone spy programming applications are certainly the least demanding and least expensive approach to do this; and you don’t need to be a tech wizard.
I have audits of the top of the line spy applications on this site. My fundamental telephone spy applications spread all that you have to begin.
Confided items how to hack a phone number
The two smash hit programs today are MPSP and FlexPy – both are confided in items that I have attempted and really utilized. To get a top to bottom glance at what these applications can do, you should look at my MSP survey and my Flexi SPY audit pages here – I think you’ll be astonished!
Both can be utilized in full covertness mode and will be practically difficult to recognize. Nobody will realize that their cell phone has been hacked. See audits to see the subtleties and costs of each hacking application. MSPS is the most famous hacking application. See what you think here to hack someones phone with just their number.
- Instructions to Hack A Telephone Picture
- How Hacking Functions With Spy Applications
- There are fundamentally two different ways for spy applications to work:
- Full form programming
This is the product that you download and introduce straightforwardly on the telephone that you need to hack. You need physical admittance to the telephone for in any event a couple of moments. Once introduced, the covert agent application gathers information from the objective gadget and transfers it to the online dashboard. You can sign in on the web (from anyplace) and see all gathered data and movement via telephone.
How to hack a phone, this is full form chips away at Android and Apple iPhone and tablet gadgets. When the product is introduced – no further access is required and you can see all information distantly. They are actually the most ideal approach to hack any telephone with no master.
There is no escape form
This is a generally new hacking technique and is just accessible for Apple gadgets, for example, the iPhone. There is no product introduced on the telephone you need to hack – and there is no compelling reason to break Apple telephones.
This form screens reinforcements of telephones made with iCloud. Apple’s free reinforcement program for iPhone, and so forth. It doesn’t give constant information since it depends on reinforcement refreshes. There are likewise less checking highlights than full form programs. In any case, it is as yet a ground-breaking hacking device.